Looking through the breaches
There’s been a lot of chatter about “the year of the breach”. The Internet Security Threat Report 2014 released by Symantec [PDF] link is summarized by Google as 2013 having 62% more data lost to security breaches than 2012.
Either this experience didn’t teach us well enough, or it taught the bad guys a lot better than it did the good. 2014 has had a very impressive run thus far with regards to data loss incidents owing to security incidents / electronic breaches. Almost every industry that engages with a high volume of users / customers has reported a major breach. From grocery stores to department stores to delivery companies to hospitals – they have all made the news recently.
This could be exacerbated by the social media explosion that we have surrounded ourselves with over the past couple of years. Social media carries news very well, and sometimes…too well when it comes to details and retaining a focus on what’s important. So, I decided to look for some facts and spot some patterns or trends that could offer some insight into the real magnitude of the problem.
Turns out that there’s a non-profit organization in California that focuses on privacy rights. It calls itself the Privacy Rights Clearinghouse and their mission is to engage, educate and empower individuals to protect their privacy. The goals of this organization are around raising consumers’ awareness of how technology affects personal privacy; and empowering consumers to take action to control their own personal information by providing practical tips on privacy protection. They also go on to respond to complaints, document complaints and advocate for consumers’ privacy rights. Their good work gets them a lot of praise, awards (2012 Albin Gruhn Award, amongst others) and keeps them in the news.
As a part of delivering on their charter of raising consumer awareness about how technology affects personal privacy, this non-profit maintains an accurate and very well-updated repository of data breach incidents. These incidents are attributed to one of the following reasons:
- Unintended disclosure – Sensitive information posted publicly on a website, mishandled or sent to the wrong party via email, fax or mail.
- Hacking or malware – Electronic entry by an outside party, malware and spyware.
- Payment Card Fraud – Fraud involving debit and credit cards that is not accomplished via hacking. For example, skimming devices at point-of-service terminals.
- Insider – Someone with legitimate access intentionally breaches information – such as an employee or contractor.
- Physical loss – Lost, discarded or stolen non-electronic records, such as paper documents
- Portable device – Lost, discarded or stolen laptop, PDA, smartphone, portable memory device, CD, hard drive, data tape, etc
-
Stationary device – Lost, discarded or stolen stationary electronic device such as a computer or server not designed for mobility.
Unknown or other
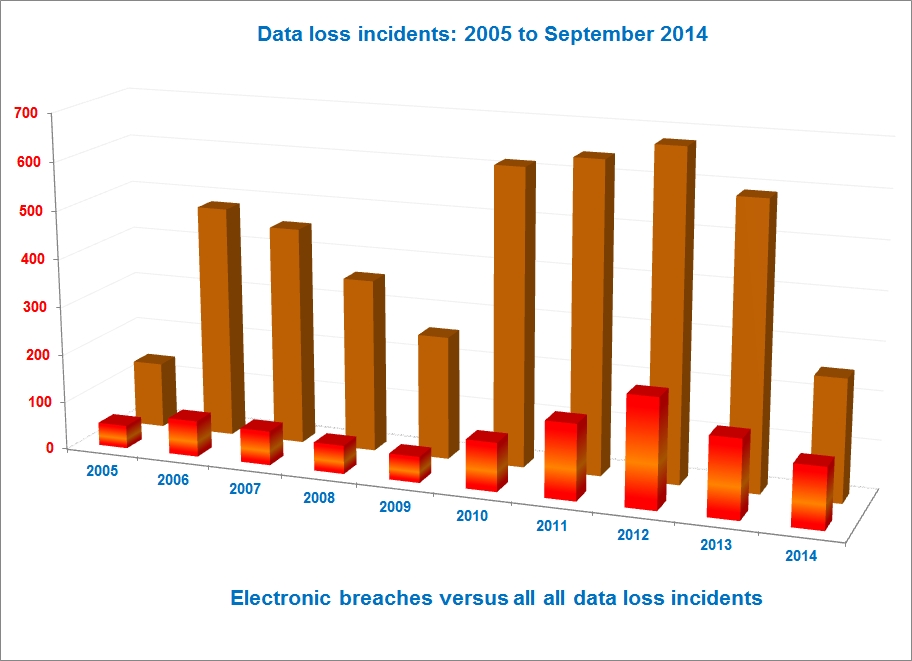
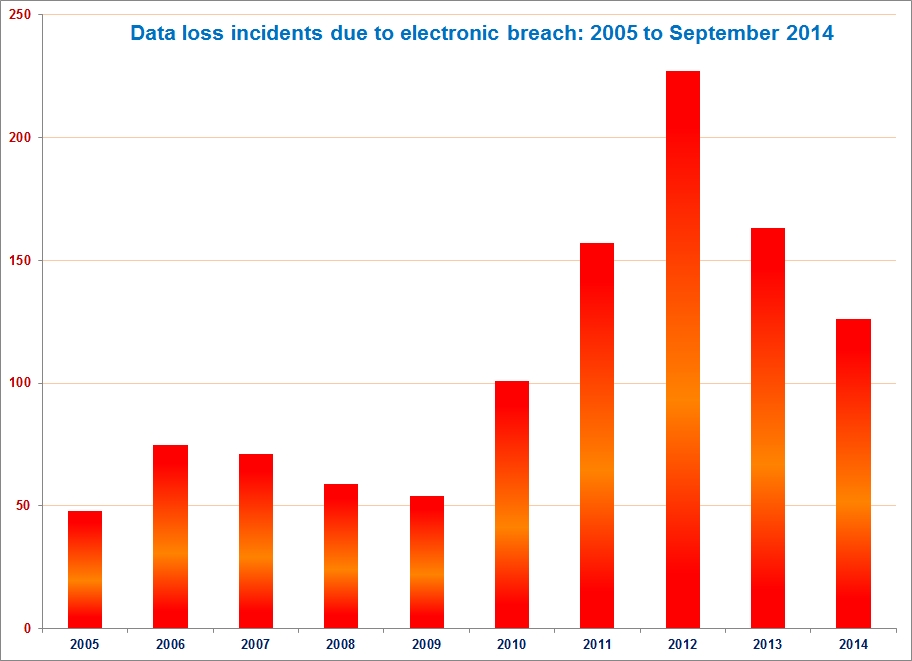
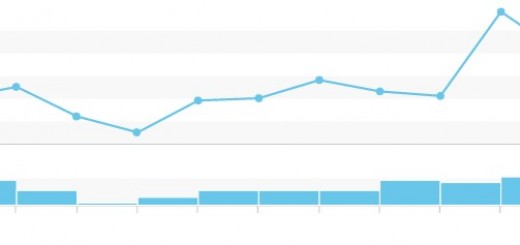
Just looking at the “Hacking or malware” category for data breaches since 2005, a few interest trends began to emerge:
2012 seemed to have the most reported data breach incidents attributed to “hacking” thus far
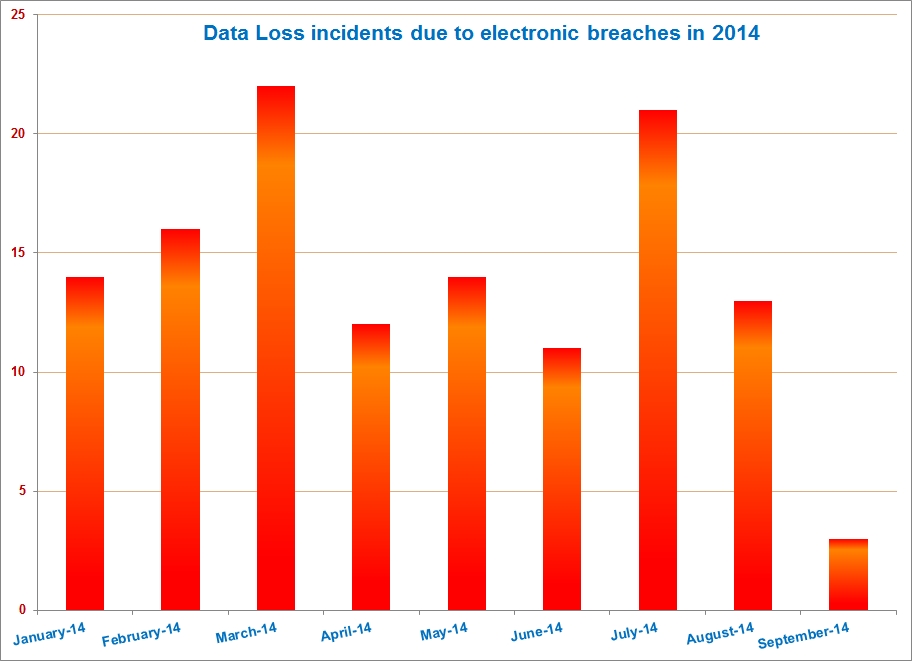
The data breach incidents reported thus far in 2014 seem to be trending down, but we’re still in September..
Data loss incidents owing to “Hacking” or “Electronic Breach” are just one slice of the pie
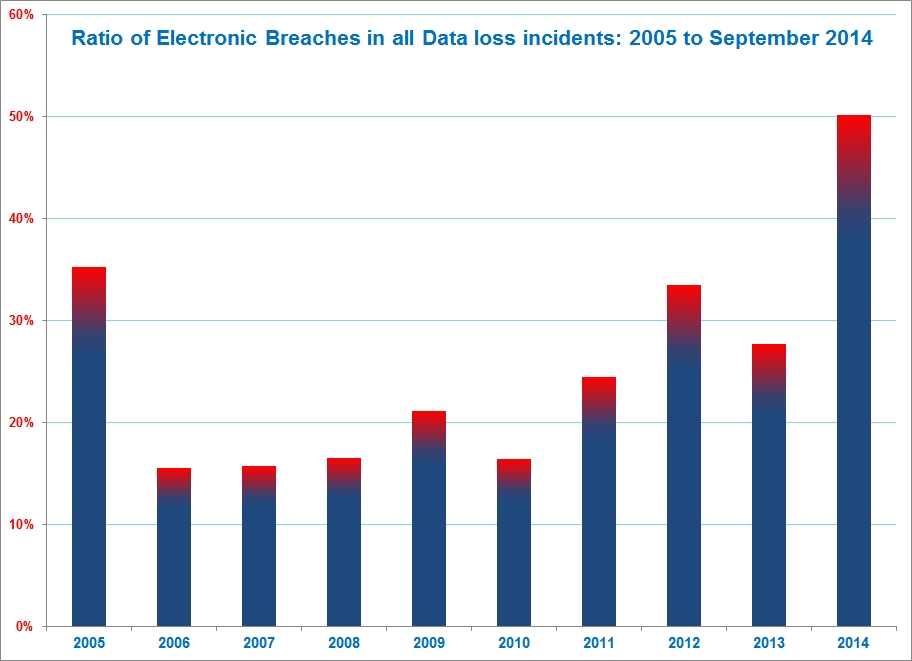
Which brings us to the real metric of interest – the ratio of electronic breach / “Hacking” as a cause for data loss incidents is the highest in 2014 as compared to the last 9 years..and we’ve still got three months to go.
So…unless we learn from the experiences of this year thus far, 2014 may be well on its way to unseat 2012 as the new “year of the breach”.






















Vox Populi