What is an IMSI catcher, anyway?

There’s been some buzz online about the unregulated sale of telecom equipment that could be used for surveillance in the cellular telephony universe; a.k.a “IMSI Catchers”. So…what are these things, anyway?
There’s a fair chance that you have a cellphone, and a reasonably good chance that your cellphone as a SIM card in it. Yes, even most of the CDMA-using folks have a SIM embedded in their iPhones now in order to be global-travel-friendly.
SIM cards get a lot of airtime (pun intended). Most kinda know what they do, how they look, where they go, how much they cost, what the process is to get one, etc. All good things if you’re traveling internationally and your parent cellphone service provider has dramatically higher telecom rates than getting a local SIM card and a paid Skype account.
A SIM card has the following information stored on it:
- Your unique serial number ICCID
- IMSI number known as International Mobile Subscriber Identity
- PIN or your Personal Identification Number
- PUK which stands for Personal Unblocking Code
- Information sent to the local carrier
- Ciphering info
- Security authentication information
The IMSI is sent to your carrier when you register your phone. It is a 15-digit number where the first five digits can tell you what carrier and country your handset is locked to.
Here’s what an IMSI is made up of:
- First 3 digits are your MCC or Mobile Country Code
- The 4th and 5th digits are for MNC or Mobile Network Code in a number of countries
- The next 9 or 10 digits are for MSIN or Mobile Station Identification Number
So, its a 15-digit code that gives out a LOT of information about your cellular network identity.
To keep things clean, here’s a quick jargon-buster. You may also hear about IMEI. The IMEI and the IMSI are very different. IMEI stands for International Mobile Equipment Identity and is a unique identifier for a mobile device. IMEI is a form of ESN (Electronic Serial Number). IMEI numbers are also typically 15 digit numbers.
So, they’re off by one letter in the same position of the acronym; and typically the same length; and are typically confined to the “arcane cellular telecom geek jargon that only nerds and spies care about”…but don’t confuse the two. Back to the IMSI and the “IMSI-catcher”…
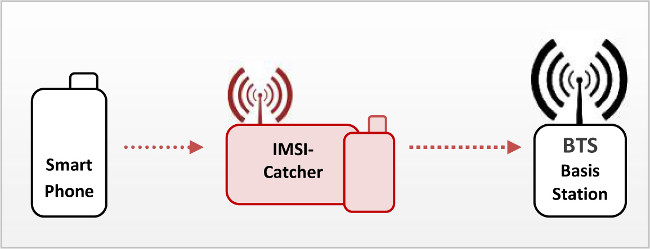
An “IMSI-catcher” subjects the phones in its vicinity to a man-in-the-middle attack, acting to them as a preferred base station in terms of signal strength. With the help of a SIM, it simultaneously logs into the GSM network as a mobile station. Since the encryption mode is chosen by the base station, the IMSI-catcher can induce the mobile station to use no encryption at all. Hence it can encrypt the plain text traffic from the mobile station and pass it to the base station.
Some of you may have thought – “Isn’t the same as someone doing that evil access point thing at a coffee shop to capture my credentials?“. Yes, and that’s why Web traffic has SSL; and that’s why logging into anything that isn’t protected by SSL is typically a very bad idea – as is using any free, public wireless access without a VPN, but I digress…
A rough visualization of an IMSI Catcher may look like this:
It sounds extremely simple, and many argue that it is – and that it shouldn’t be. Here’s a beta project by some folks who have worked to create an IMSI-Catcher detector to warn the user of such a man-in-the-middle attack.




Thanks for mentioning and linking our project! 😉
Note: We’re always seeking Android developers.